Were you ever curious to see what lay behind the face of an old mechanical Grandfather clock or even a pocket watch? – How the mechanism worked and how all the complex set of gears, springs, and wheels meshed and worked in tandem? If the mechanism was designed and built right, then everything would work to precision: “Like a Swiss clock” people used to say.
A network is somewhat like that too. If properly designed and built, it should all work with great precision like that legendary Swiss clock. In many ways, however, the network is much more complex (and prone to the occasional ‘glitch’). This is not so much due to the many parts and how they interact to handle the data – but often the data itself, the traffic loads, security protocols, failover, and so on.
Just like the watchmaker that has a set of tools and a magnifying loop to get a better look at what’s happening inside a watch and fix it (if required), the network administrator has his or her set of tools that enable network visibility.
The Network Visibility Layer – Setting the Clock Correctly
On a high level, what the visibility gives you, is the means to verify (monitor and inspect, collect data and statistics, analyze and report) and – if required – make the necessary adjustments and fixes to ensure that the right data traffic reaches the right tools.
Because of the complexity and vastness of most networks, a single “magnifying glass” is not enough. Instead, a combined set of tools and utilities work together, virtually in parallel with the network, and comprise the network visibility layer. Imagine some clock technician showing up every once in a while, to check that the clock is showing the right time, and if not, makes the necessary adjustments to the clock mechanism, so you always have the right time.
The network visibility layer is vital to your network performance. As mentioned, it is not a single device, but made up of a combination of devices, each specializing in particular aspects of network activity. That layer, however, is not just passive but offers tremendous – almost proactive – benefits to the workings of the network.
Let’s take a look at a few of those benefits. Often the same network visibility devices can support multiple business use cases.
1) Prevent Performance Erosion
You have quite a few tools, both in-line and out-of-band, that are constantly at work to secure your network and ensure its performance. Every tool is designed for an optimal mix of traffic in terms traffic type and packet size. Every tool is designed for an optimal feature mix, where some features are more processor intensive than others. If your tools are trying to handle and process more traffic than they are optimally designed for, their performance effectiveness erodes and with that erosion, your network becomes more vulnerable.
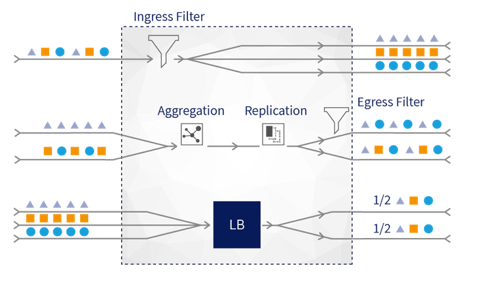
In order to ensure your network tools are performing as desired and providing the security and performance analysis needed, do not overload your tools. You need a Network Packet Broker that can handle the following essential tasks:
- Filters the data in order to send only the right traffic to the tools
- Load balances the data flow so that it can distribute the traffic between multiple tools, to share the traffic and processing load
- Load balances to deploy multiple lower capacity tools (see also point 4, below)
2) Pay-as-you-grow Deployment
You’ll also want to reduce your total cost of ownership by in terms of expending CAPEX and OPEX only on the network tools that you need. One of the major line items affecting your total cost of ownership (TCO) is over provisioning your network through FUD (fear, uncertainty, and doubt), and deploying expensive network tools today that may be used at some time in the future... What if you could use the network visibility layer to reduce your TCO, and only deploy the network tools in accordance with your real traffic loads. As the network traffic load actually increases, and only then, to invest in connecting more network tools, with safety and confidence.
Again, you’ll want a Network Packet Broker to exploit its load balancing capabilities to:
- Deploy multiple lower capacity tools (This is much more cost effective than changing to a single high-cost tool)
- Increase the number of tools and load balance traffic between those tools – as required (Invest as your network needs grow)
3) Resilient Network Design
You can use the network visibility layer as a building block in creating a resilient network design. For example, you can set up various advanced redundancy schemes such as 3+1. Four network tools are processing the traffic, and if one network tool fails the remain three tools can process the traffic load by distributing the traffic of the failed network tool. This allows for one network tool to failover (or be taken down for maintenance) without affecting the security or monitoring services used on the network. To maximize network design flexibility, connected network visibility devices can detect the status of each other and configured to forward the right traffic to the right tool based on their status.
To set this up, you will want to implement a combination of a Network Packet Broker with an integrated bypass solution. This tool redundancy setup will enable you to:
- Easily distributed traffic among multiple network tools (packet broker’s task)
- Redistribute the traffic going to the failed tool, to the remaining tools, in case one of them fails (bypass solution’s task)
4) Upgrade Avoidance
If and when you decide to upgrade your network infrastructure from a lower rate to a higher rate, implementing a solution using a Network Packet Broker will help you to postpone (and in some cases even avoid) the need to also upgrade your network tools. The network visibility layer can mediate/convert traffic from higher rate interfaces to lower rate interfaces. As long as the higher rate links are not fully utilized (bandwidth-wise) you can keep on using the lower rate traffic feeds of your network tools. Since the packet broker knows how to distribute traffic to lower capacity tools, you won’t need to upgrade immediately – or at all.
5) Inline Intervention
In a similar scenario to point 3, above, combining Network Packet Brokers and Network Bypass Switch capabilities offers special treatment for network availability if an inline tool is down or requires maintenance. In addition, the Network Bypass Switches may also offer double-protection bypass technology. Network devices are bound to fail eventually, and because inline network devices create single points of failure, implementing a double-protection bypass technology is critical to ensure your network never goes down, and network performance is never compromised. A network bypass eradicates these single points of failure by redirecting network traffic should that inline device become incapable of processing or passing traffic.
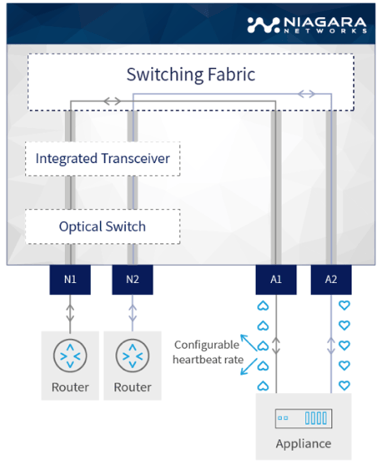
6) Secure Visibility for Critical Locations
For the deployed network tools in your visibility layer to have the maximum leverage and effectiveness, they need the ability to ‘see’ traffic from all the critical points on your network. The visibility points need to be able to handle all the traffic on the link without packet loss or performance issues. Network taps are recommended for these network visibility points. They provide a more secure and reliable method to monitor network traffic than SPAN ports. In other cases, critical network traffic information is available in a remote location, while the Network Performance and Monitor Diagnostics (NPMD) is deployed in a central location. Using a network packet broker, you can tunnel the required traffic for analysis from the remote site to the central site.
** BONUS: Fan Out (also known as Break Out)
There are various scenarios where Network Packet Brokers, Bypass Switches, and Network Taps are recommended for robust network visibility (whether singly or in combination). Your network design will depend on your requirements and budget, as well as your expected future network growth.
Niagara Networks would like to introduce you to a bonus capability available on our 40Gb interfaces available on the model 4432 packet broker and on the N2 series 2845/2847: the ability to Fan Out (also known as Break Out or “break”) a 40Gb link/interface into four 10Gb links. This enables flexibility in supporting 10Gb feeds, as needed. It is also applicable to our Bypass switch segments – turning a 40Gb bypass segment into 4 x 10Gb bypass segments.
For more information on the 4432 packet broker, and in general, how Niagara Networks can help you with your network visibility layer needs, feel free to contact us or visit our resources webpage.
For more information on deploying and optimizing your network security tools for better protection and availability, contact Niagara Networks to arrange a consultation today.

 By: André Vink
By: André Vink