Today, with network security becoming more important than ever before, enterprises are deploying a variety of network security tools. This is because security threats are becoming more robust, and networks are needing to cope with exponentially increasing amounts of complex data flowing through the network.
In this post, we’ll shed light on how to cope with the above challenges by taking advantage of a few simple principles:
1. Implementing Out-Of-Band Security
The out-of-band monitoring approach allows network security teams to connect security tools ‘Out of band’ meaning: the production networks are tapped and brokered into. This type of architecture also enables maintenance and upgrade actions to be performed on monitoring tools without impacting the production network in any way.
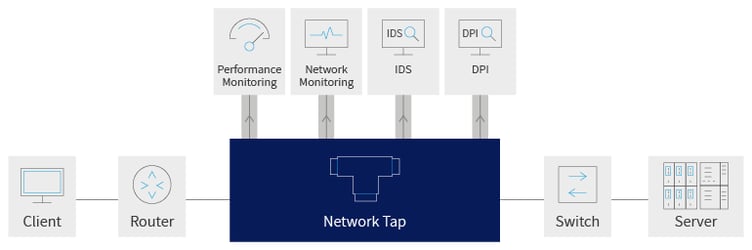
A packet broker can be configured to perform load balancing between multiple tools ensuring that each tool gets the traffic it designed to analyse.
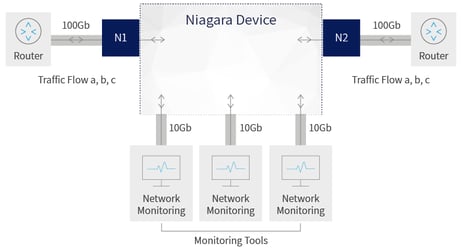
Also, this architecture also allows connecting lower rate security tools to higher rate network links, and adding more capacity as needed. The “out of band” deployment also means that if any of the tools is experiencing downtime, it will not impact the live network and traffic will not be interrupted.
2. Offload “Lower Level” Tasks to Packet Brokers
First let’s remind ourselves what is a network packet broker:
It is a device that forwards network traffic from switches and routers to various network monitoring and security tools. The packet broker can impact the traffic going through by, for example, applying filtering rules, replicating traffic streams to multiple tools, or aggregating traffic from multiple sources to output destinations.
High end packet brokers can handle jobs like deduplication, packet slicing and data masking. Additional functionality of high end packet brokers can include NetFlow generation and aggregation. Packet brokers are likely to perform those tasks much more cost effectively than security tools that are typically optimized for handling higher OSI layer tasks.
If for example, your network has 20% traffic duplication, then your a security tool is working harder on processing that traffic twice. With the packet broker off loading the security tool and performing deduplication the security tool’s efficiency is increased twice. It’s not processing traffic that is not needed and it has freed up capacity and availability to do more ‘security’ work and higher level tasks.
Make sure that before you select the right packet broker for your needs, you study which of these functions are needed in your case. Off-loading various packet filtering and slicing tasks within the packet broker will mitigate cases where security tool performance is impacted because of overflow, thus reducing the ‘security efficiency’, and possibly exposing your network and users to threats..
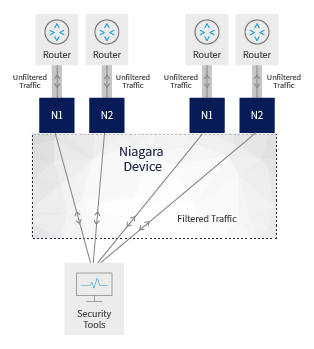
3. Filter out Unnecessary Traffic
It is highly recommended to send to each tool exactly the traffic that it needs to see, and not more than that. A packet broker can be used effectively in order to separate “low risk” streaming traffic such as: music, voice, video, or traffic from trusted sources - and send to the security tools only the traffic which holds higher risk.
For example, let’s say you have a tool that performs detection or prevention of intrusions that are coming in through HTTP. On the other hand, VOIP or streaming traffic are not expected to be suspicious of carrying the type of threats that this tool deals with. In this case the packet broker can filter away all the SIP and RTSP traffic. This will free up tool capacity to deal with more of the relevant traffic and will allow for much more effective usage of the more expensive security devices.
4. Better Security Visibility with Lower TCO
One of the great benefits that building a visibility fabric which can be managed by SDN, is the ability to serve multiple network segments from a single location.
This architecture offers security network managers the ability to deploy high end security tools with dedicated functionally efficiently, and use them to serve data traffic from multiple network segments and multiple locations. This can assist in optimizing the utilization of expensive tools, rather than deploying smaller less capable tools for each segment.
For example, if you place a high capacity IPS system in a data center that can then serve multiple network segments, you can have it duplicated for redundancy, and also it can share its more efficient processing and high end capabilities on traffic from the entire network. So instead of configuring 1+1 IPS system for each segment separately, you can configure one 1+1 system with higher capacity to serve all network segments.
For more information on deploying and optimizing your network security tools for better protection and availability, contact Niagara Networks to arrange a consultation today.
.jpg)
 By: André Vink
By: André Vink