Challenges of Encrypted Traffic Visibility and Threat Detection
Encryption has fundamentally changed the way traffic visibility works. Nearly all modern network communication - web, cloud, SaaS, internal services - is encrypted by default. While that’s great for user privacy, it complicates lawful intercept workflows. Getting access to the right traffic, extracting meaningful data, and staying within legal and privacy boundaries is no easy task.
Legacy visibility approaches are no longer enough. A simple TAP or SPAN port won’t help when the payload is encrypted, and full decryption at scale often introduces legal, ethical, and operational risks. What’s needed is a smarter way to see what’s happening, without necessarily seeing everything.
Advanced Packet Brokers: Traffic Selection, Filtering & Packet Pre-Processing
This is where Advanced Packet Brokers provide the right visibility layer to cope with emerging challenges. Instead of sending a full-pipe of traffic to your monitoring tools, Advanced Packet Brokers give precise control over which traffic is delivered to the right tool. You can TAP only the relevant sessions, apply filtering based on IPs, ports, VLANs, or extend visibility to layer 7 DPI-based application IDs, and reduce the burden on your analysis stack by slicing out the unnecessary payload.
Advanced Packet Brokers can also handle complex encapsulations like GRE, VXLAN, or MPLS and ensure that you’re seeing both outer and inner traffic layers, which is especially useful when tunneling is used to hide threats.
Encrypted Traffic Visibility: TLS Decryption and Metadata Extraction
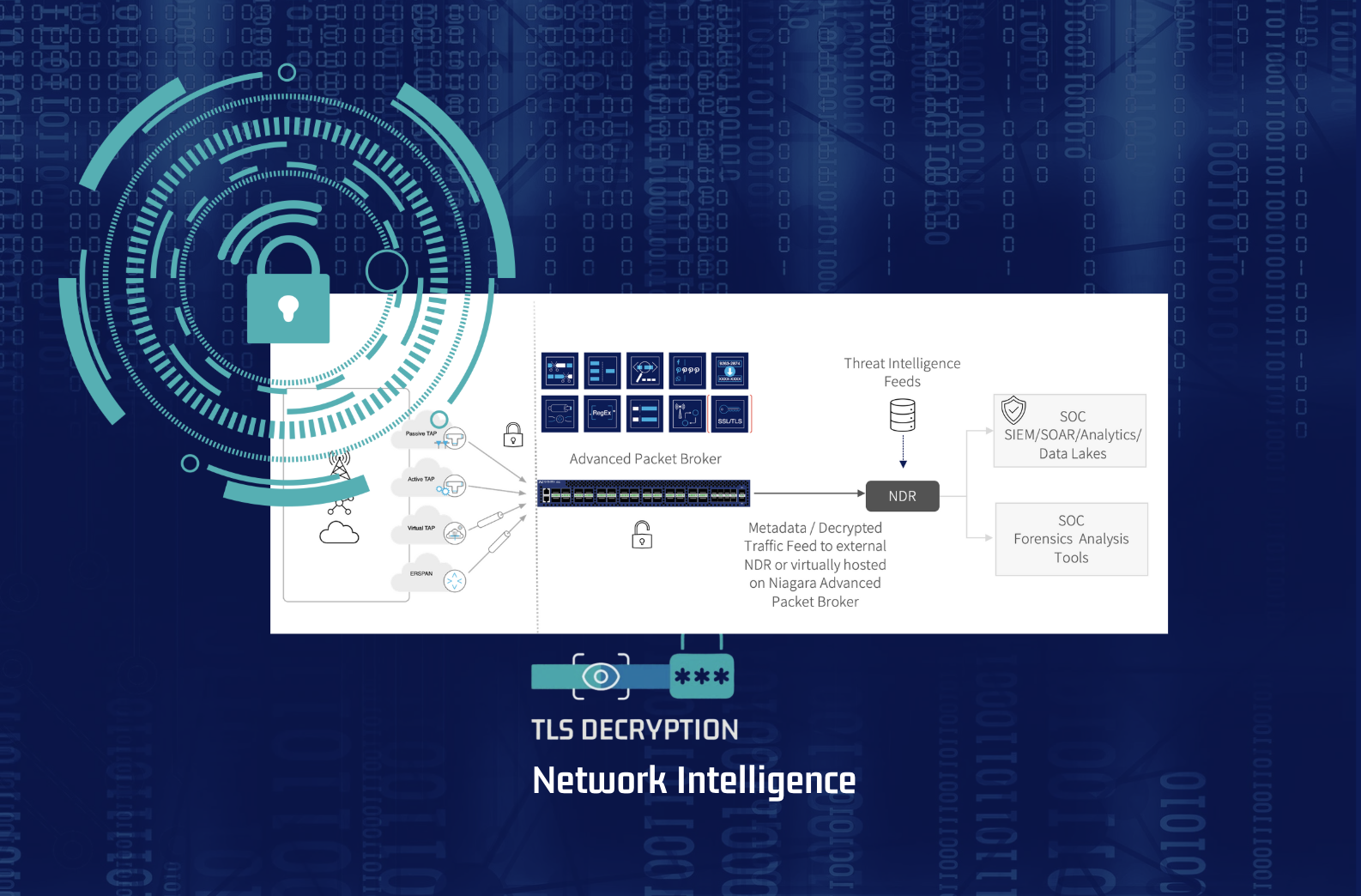
Niagara Networks' Advanced Packet brokers offer two primary methods for visibility into encrypted sessions.
First, when decryption is permitted, the packet broker can operate as an out-of-band passive TLS decryption engine or as a man-in-the-middle TLS proxy, terminating and re-establishing encrypted sessions. The decrypted traffic can then be forwarded, masked, or selectively filtered based on policy. This enables deep inspection for critical flows while maintaining control over data exposure.
Second, when decryption is not allowed or simply not practical, Niagara's packet broker can still extract high-value metadata from intercepted data flows. That includes the TLS fingerprints, Server Name Indication (SNI), certificate attributes, flow durations, and more. Metadata provides a strong signal for behavioral analysis without violating encryption or privacy constraints.
Encrypted Traffic Analysis: The Synergy Between Niagara and Network Detection Tools
This is where the combination of Niagara's Advanced Packet Brokers and a Network Detection and Response (NDR) platforms really shows its strength: Advanced Packet brokers will perform the interception of traffic of interest and share it with NDR tool. The NDR is designed to work effectively in encrypted environments by focusing on Encrypted Traffic Analysis - a technique that uses metadata and behavioral patterns to uncover threats without accessing packet payloads.
The Network Detection and Response platform can then perform the following types of analysis:
-
JA3, JA3S fingerprinting to identify clients, servers, or known malware toolkits
-
TLS metadata such as session timing, flow size, and certificate properties
-
SNI extraction to understand traffic destinations
-
Machine learning to classify session types and detect unusual patterns like command-and-control or lateral movement
This method reduces operational risk, eliminates blind spots created by encryption, and improves detection accuracy. It also ensures that sensitive payloads are never unnecessarily stored or processed.
That said, encrypted traffic analysis doesn’t cover everything. For some encrypted protocols, deeper visibility may still require full decryption. But for most TLS 1.3 or HTTPS traffic, the combination of packet broker generated metadata and NDR analytics offers powerful insights.
Workflow: Packet Broker & NDR Integration for Encrypted Traffic Visibility
Here’s how this works in practice:

Traffic enters the network through high-speed links and is ingested by the Advanced Packet Broker. In this stage it performs filtering based on authorized selectors - IP, port, VLAN, or more complex policy tags. Depending on configuration, it may decrypt traffic or extract/generate metadata in real time. The processed stream is cleaned, reduced, deduplicated (if required) and compliant and sent to NDR.
In the final stage, the Network Detection and Response platform performs behavioral and fingerprint-based analysis, looking for anomalies or known patterns. If a JA3 hash matches a known malware framework, or if a certificate looks suspicious, it generates an alert. All of this happens without full packet inspection.
This workflow balances visibility, security, and compliance in one modular architecture. Niagara Networks advanced packet brokers enable as part of the Open Visibility Platform to host virtual NDR as single unified platform, meaning the entire process is performed within contained environment or to use two separated platforms that are connected via network interfaces and obviously consume more space, power and other operational burdens. In any case, solution can be delayed based on NetSecOps teams architecture preferences.
Traffic Flow Optimization and Privacy Preservation Through Metadata Analysis
In today’s encrypted world, the less content you store, the better. Packet brokers allow SeOps to push only what’s needed - JA3 hashes, NetFlow records, SNI values - into security inspection and detection tools. This supports privacy laws, reduces tool fatigue, and avoids storing content organizations not legally allowed to inspect.
But metadata isn’t harmless. Research shows that even without decryption, metadata can reveal surprisingly deep insights into user behavior, communication patterns, and device associations. Over time, it can be used to identify users, spot group behavior, and map routines. The real risk? Metadata often lacks the same legal protections as content, meaning organizations have to self-regulate its collection and usage responsibly.
And it goes deeper. Even seemingly harmless digital fingerprints, like browser or TLS handshake characteristics, traffic frequency, or session timing, can reveal a user's identity. Misconfigured tools or overly detailed metadata capture can quietly unravel anonymity. That’s why metadata hygiene and precision aren’t optional - they’re operational security essentials.
This is exactly why our architecture emphasizes discipline in metadata exposure. The Advanced Packet Broker extracts only what is operationally required, and the NDR platform analyzes traffic behavior through metadata and fingerprinting rather than raw content. Together, they enable robust detection while maintaining strong privacy controls and compliance posture.
Combined Architecture Benefits: Detection Accuracy, Compliance & Operational Efficiency
Here’s how Niagara Networks' Advanced Packet Brokers and NDR platforms work better together:

This joint architecture enables encrypted traffic visibility and threat detection that is scalable, effective, and privacy-aware.
Conclusion: A Scalable and Intelligent Framework for Encrypted Traffic Detection
Legacy approaches that rely on payload inspection are no longer suitable for modern network environments. Instead, metadata and fingerprint-based visibility form the foundation for modern threat detection workflows.
Niagara Networks’ Advanced Packet Brokers, equipped with deep packet inspection up to layer 7, TLS decryption, packet slicing, NetFlow/IPFIX generation, and complementary fingerprinting packet data, act as the central intelligence visibility fabric layer. Combined with behavioral NDR platform, this architecture delivers:
-
High-fidelity traffic visibility with minimal exposure
-
Detection without decryption
-
Context-rich monitoring in real time
-
Compliance
---
Niagara Networks are industry specialists in network visibility, providing advanced network visibility solutions for the specific needs of individual enterprises and national large and complex networks.
Don’t leave your network vulnerable to security threats, schedule a consultation with one of our network visibility experts today to evaluate your network visibility challenges.
 By: Zeev Draer
By: Zeev Draer