Distributed Denial-of-service (DDoS) attacks continue to accelerate and evolve into highly sophisticated vectors, threatening any digitally connected entities and services; specifically, the entry of connectivity to the global /local communications networks [which start with the Communications Service Providers (CSPs)] that are defined as underlay “gateways” with a clear demarcation edge of networks. Discussions with Security Operations Centers (SOCs) in various regions raise the same trend; all SOCs face a tsunami of alarms issued about an enormous increase in DDoS attack threats against a wide spectrum of organizations across industries and vertical markets globally. This trend continues to become more severe with the reality of the “record-breaking” 2.4 Tbps DDoS volumetric attack that targeted Microsoft Azure in the European region during the 2nd half of 2021, and the later DDoS attack that was detected and blocked by Cloudfare, which peaked at just under 2 Tbps. As we are entering the 3rd year of the pandemic, we are witnessing the impact and unavoidable evolution of the "COVID-effect", which is increasing the diversity of multi-vector attacks as massive digital transformation changes/removes the traditional boundaries of organizations. Attacks are becoming destructive and in higher cycles than ever. As a result, manual/static processes of DDoS mitigation are no longer valid, and many organizations are moving towards a DDoS auto-mitigation strategy that can cope better with the volume and the diversity of attacks.
To understand the design of networks and correlation to traffic flows, we can absorb where it might be critical to forming an active DDoS mitigation strategy. Reviewing the network architecture layers of CSPs in the below diagram, we can see local Internet Service Providers (ISPs) and the aggregated connections to the international Internet Exchange (IX) gateways to the global internet.
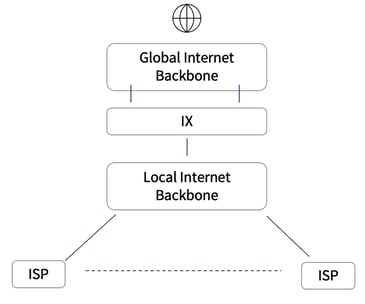
In various cases, ISPs monitor and control the traffic and can mitigate any DDoS activity ingress and egress to the localized networks. A centralized DDoS mitigation approach for national internet traffic can be efficient but certainly requires the local incumbent authority to step in and define a strategic shield of regulation and synchronized mode of operation. To accomplish this mitigation strategy, network architectural design requires three essential stages of probing the production traffic, detection of situational patterns, and reaction to mitigate the hostile traffic of DDoS attacks.
To reflect the strategy in a visual scheme, we can see that the local internet (national internet) backbone includes two critical connectivity elements, the distribution router and the border routers that route the ingress and egress traffic. As a result, placing an interception TAP in this segment can enable collection/sensing of the essential traffic data for our detection stage strategy of anomalies or any suspicious signs to react upon.
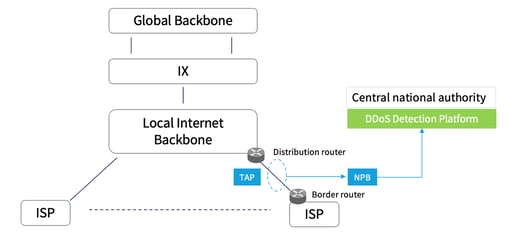
The three essential stages of design and deployment strategy:
- A strategic interception point will be introduced in the path of the Border router and the distribution router. Deployment of optical or electrical TAPs will enable the copy and redirection of all traffic into a Network Packet Broker function that will parse the packet data and can even generate metadata as flow traffic to the central national authority which can then be locally defined or even tunneled to any external premises. Placement of TAPs can be in the segments of the national backbone or in the Internet exchanges’ central points.
Niagara Networks visibility offering can include a standalone dedicated TAP or an intelligent TAP that offers a highly integrated TAP and packet broker appliance. In both cases, the design and deployment of a TAP will not introduce any latency or point of failure in the line of traffic between the border router and the distribution router. - Probing and metadata generation will enable a flow-based detection strategy. Metadata generation can be activated in the border routers with NetFlow metadata aspects, but to offload this function from routers, the Niagara Network Packet Broker can perform such tasks in a more effective way and hand over the meta flow to the central national authority for DDoS detection and response. Flow data collected from all interception points will be aggregated and sent to a DDoS detection platform that is owned and operated by the central authority.
The importance of integrating an advanced packet broker is it can streamline and effectively parse the packet data to deliver only the relevant traffic to the DDoS detection and response platform. This is a critical function to enable efficient detection and faster response to DDoS attacks. An advanced packet broker can perform a high-definition inspection, thus if the attack is related to application layer APIs, only that specific layer of traffic will be delivered to the API DDoS detection and response platform. Such a layered approach enables security and network architects to design a holistic and scalable DDoS detection and response architecture, specifically, when there are many ISPs that will be sampled to reflect the real status of a wide spectrum of networks and traversed digital services. - Detection and response is the last stage for data flow anomaly analysis. Machine learning, threat intelligence, DNSBL analysis, and many other technologies will be used for the detection of DDoS attacks and Botnet activities. Responsive strategy can be based on routed BGP FlowSpec (based on RFC5575 ) mitigation strategy along with cloud-based scrubbing services. To carry out the right network architecture for the central authority DDoS platform, it will be configured as a neighbor for all ISPs and will enable, in the case of substantial attack traffic detection, the activation of the BGP FlowSpec announcement to the respective ISP. This functionality will reroute to the most optimized configuration considering route threshold and in the scenario of a massive attack, cloud-based scrubbing services will be initiated by rerouting to the scrubbing center. This stage can be balanced with respect to the economic considerations of scrubbing services that can be offered by cloud providers or security service providers. In certain cases, an advanced packet broker can participate in a proactive response to an attack via a REST API automated policy rule to redirect or filter the hostile traffic. Such functionality can streamline distributed DDoS response or be part of the entire set of tools of security and network operational teams.
In Conclusion
Modern DDoS defenses require intelligent automation to cope with the increasing complexity and volume of DDoS attacks. National large complex networks can be controlled with adequate inclusion of the visibility building blocks as part of DDoS defenses with sophisticated design and implementation. To learn in more detail from our experience in assisting national complex scenarios, please contact our network visibility experts.
Niagara Networks are industry specialists in network visibility, providing advanced network solutions for the specific needs of individual enterprises and national large and complex networks. Don’t leave your network vulnerable to security threats, schedule a consultation with one of our network visibility experts today to evaluate your network visibility challenges.

 By: Zeev Draer
By: Zeev Draer