Network security isn’t just about stopping hackers; it’s about ensuring visibility into every packet moving through your digital infrastructure. Many IT teams, specifically NOC teams, default to using SPAN (Switch Port Analyzer) ports because they seem convenient and cost-effective - but convenience can come at a steep price when packets start to drop and security is at risk. Let’s dive into the limitations of SPAN ports, why they fall short, and when to use network TAPs (Test Access Points) instead.
The Downside of SPAN Ports: Risks and Limitations
At first glance, SPAN ports seem like a quick fix. However, their drawbacks make them less suitable for today’s high-demand networks. Here’s why:
- SPAN Takes Up Valuable Ports: High-value switch ports could be better utilized for actual network traffic rather than monitoring.
- Legacy Limitations: Some older switches don’t even have SPAN ports.
- Dropped Packets: Perhaps the biggest issue - SPAN ports frequently drop packets, particularly when they are oversubscribed.
One of the primary reasons SOC teams steer clear of SPAN ports is packet loss, which often occurs when the port is overloaded or under strain. In virtualized environments, traffic utilization can spike due to the dynamic nature of short-lived flows in East-West traffic, originating from spinning up new services, containers, and virtual machines running on high-capacity 10GB, 25GB, or 50GB server interfaces. On the other hand, even in operational technology (OT) environments running at 10 MB, 100 MB, or 1 GB, packet loss is a common risk.
Why Do SPAN Ports Drop Packets?
- Memory Shortages: Limited buffer space can result in packets being dropped.
- 'PAUSE' Frame Attacks: Malicious actors can exploit SPAN ports by flooding them with loopback signals, hiding malicious data and forcing legitimate packets to drop.
- Broken Cyclic Redundancy Check (CRC): Packets with CRC errors are automatically discarded.
- Frame Size Issues: Frames smaller than 64 bytes or larger than the maximum transmission unit (MTU) jumbo frames may be dropped.
And if that wasn’t enough, consider these additional concerns:
- Corrupt Packets Are Ignored: SPAN ports won’t forward corrupt packets or errors, potentially hiding signs of attacks.
- Packet Duplication: When monitoring multiple VLANs, duplicated packets can confuse analytics tools.
- Timing Alterations: SPAN ports can alter the timing of frame interactions, skewing response time analysis.
The Real Security Risk: SPAN Port Vulnerabilities
Beyond the technical drawbacks, SPAN ports introduce security vulnerabilities:
- Bidirectional Traffic Risks: SPAN ports can inadvertently allow traffic back into the network, exposing switches to potential attacks.
- Increased Administrative Costs: SPAN port configurations require ongoing maintenance and adjustments, which can be resource-intensive.
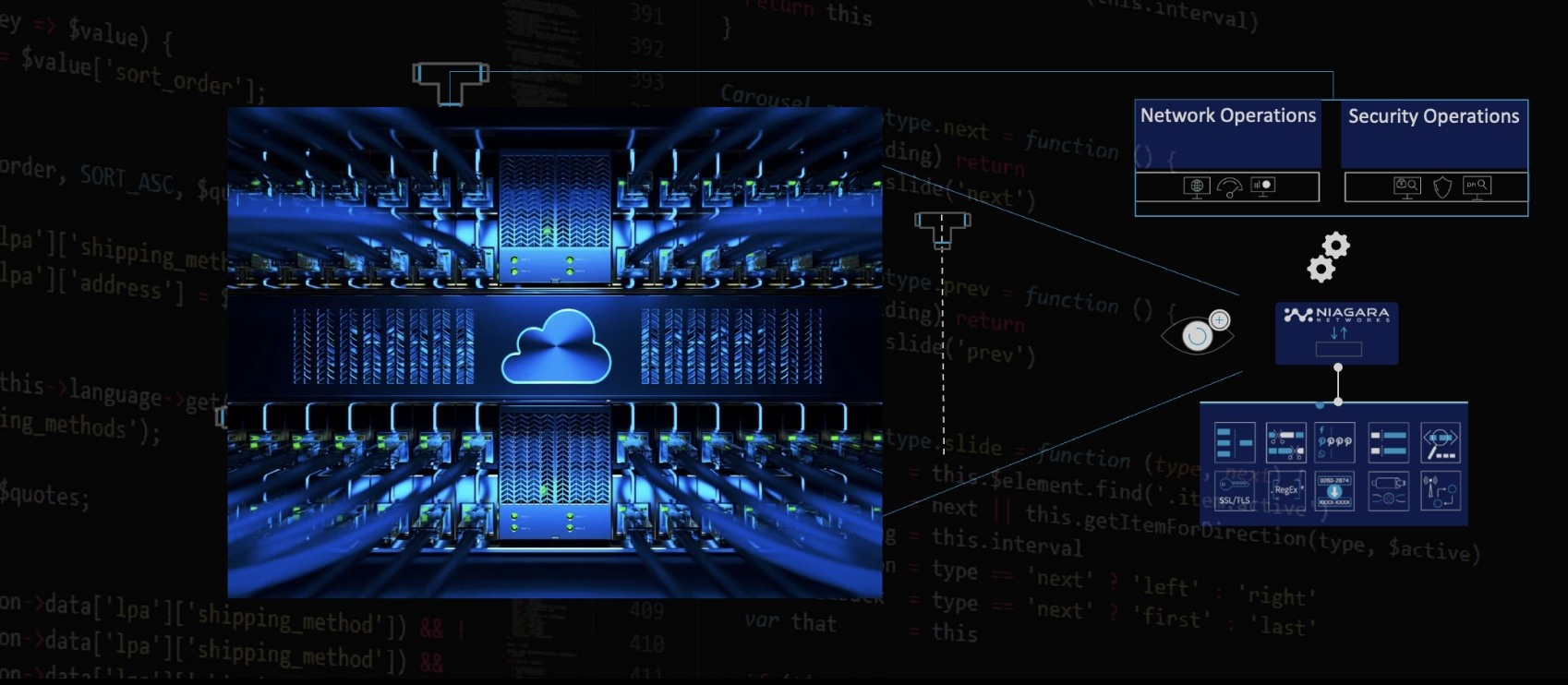
Adding Network TAPs: The Gold Standard for Packet Visibility
For a reliable solution to packet monitoring, network TAPs are the industry’s best practice. Here’s why they outperform SPAN ports:
- Exact Traffic Duplication: TAPs create a 100% accurate, full-duplex copy of network traffic without altering the data.
- No Packet Drops: Unlike SPAN ports, TAPs don’t drop packets - they deliver every bit of data as it flows.
- Scalable Monitoring: TAPs can generate single or multiple copies of traffic, aggregate streams, and optimize the performance of monitoring tools.
Network TAPs deployed strategically between network segments and passively copy traffic without disrupting the network, ensuring uninterrupted visibility. Their simplicity and reliability make them a set-it-and-forget-it solution
When to Use SPAN Ports (Yes, There Are Exceptions...)
There are scenarios where SPAN ports can be acceptable, such as:
- Temporary or Ad Hoc Monitoring: Quick troubleshooting in environments where a TAP isn’t available.
- Limited Light Budgets: In optical networks with tight light budgets, SPAN ports may be preferable to splitting light via TAPs.
- Production Emergencies: Immediate access to traffic when a TAP installation isn’t feasible.
- Remote or Low-Traffic Locations: Sites where the cost of deploying a full-time TAP may not be justified.
- Traffic Within a Switch: Monitoring internal switch traffic not accessible via physical links.
The Rule of Thumb: TAP Where You Can, SPAN Where You Must (last resort)
In modern, high-speed networks, TAPs should be the default choice for ensuring full visibility and security. Here are key reasons why:
- Full-Fidelity Traffic Monitoring: TAPs capture exact copies of bidirectional traffic, enabling accurate monitoring and analytics.
- Continuous Access: Once installed, out-of-band TAPs don’t require ongoing configuration or maintenance.
- No Oversubscription: Unlike SPAN ports, TAPs don’t drop packets, ensuring reliable monitoring.
- Consistent Line Rate: SPAN ports often underperform, especially when prioritized below production traffic.
- Minimal Network Impact: TAPs operate passively without affecting network performance.
- Regulatory Compliance: TAPs meet legal and corporate requirements for comprehensive traffic monitoring.
- Protocol Agnostic: TAPs capture all traffic, whether IPv4, IPv6, or packets with errors.
Final Recommendation: Choosing TAPs for Maximum Network Visibility
For organizations seeking consistent, accurate, and secure packet visibility, Niagara Networks TAPs provide an optimal and reliable solution. Any time traffic volumes are moderate to high, deploy network TAPs and ensure you never miss a packet. For low-traffic or temporary needs, SPAN ports can fill the gap, but never rely on them when visibility and security are mission-critical. For networks that demand 100% visibility, scalability, and security, TAPs are the smart investment...
Schedule a consultation with our network visibility experts to uncover and resolve your visibility challenges.
 By: Zeev Draer
By: Zeev Draer
