More and more network traffic is encrypted as people and businesses try to keep their data private and secure as it travels through the Internet. By encrypting transmissions, sensitive information, such as a user's login ID for an online banking session, or perhaps a credit card number, is protected and kept out of the hands of potential hackers and criminal organizations. By 2019, Gartner believes, more than 80 percent of enterprise web traffic will be encrypted.
Secure Socket Layer (SSL) is the de facto standard for ensuring the security of traffic across the Internet. SSL and Transport Layer Security (TLS) have long been used to secure Internet-based transactions such as for e-commerce and online banking (for simplicity, we will use “SSL” to refer to both SSL and TLS).
Over time, the simplicity that SSL provides has made it the perfect vehicle to migrate many applications to a web-based model for new online services like viewing medical records, ordering prescriptions, filing federal, state, and local tax returns and other government uses. In addition, new cloud-based and enterprise applications such as Salesforce.com, Sharepoint and most of the web-based email applications on the market such as Gmail, Yahoo, etc.
SSL Fundamentals
SSL delivers encryption, authentication and data integrity in a Public Key Infrastructure (PKI). PKI is a set of policies and procedures that establishes a secure information exchange between devices. Three fundamental elements characterize the PKIs used in asymmetric cryptography:
- Confidentiality. In SSL, large amounts of data are encrypted using one or more symmetric keys that are known only by the two endpoints. For SSL, the sender encrypts the symmetric keys with the public key of the receiver to ensure that the private key of the receiver is the only key that can decrypt the transmission.
- Authentication. This refers to the ability of the client and server devices in the secure information exchange to verify the identity of the other device. For example, assuming an SSL client is connecting to an e-commerce website, before sending sensitive information such as a credit card number, the client verifies that the server is a legitimate e-commerce website. SSL facilitates this authentication through the use of digital certificates issued by a certificate authority (CA).
- Message integrity. Assurance that the contents of the message have not been tampered with during transit is critical to enabling secure communications. To ensure message integrity, SSL applies a message digest which takes an arbitrary-length message and outputs a fixed-length string that is characteristic of the message to all communications.
A HTTP-based SSL connection is always initiated by the client using a URL starting with https://. At the beginning of an SSL session, the client and server use the SSL handshake protocol to negotiate the SSL parameters that they will use during the secure session.
.png?width=600&name=Blog%20%2340%20-%20The%20challenges%20of%20SSL-01%20(2).png)
Figure 1. SSL Handshake Overview
SSL Inspection Imperative
While the use of SSL is crucial for ensuring secure communications over the Internet, encrypting sensitive transactions can allow them to pass through enterprise security measures unchecked. This fact is exacerbated because SSL-encrypted communications constitute a significant and growing percentage of the traffic in enterprise LAN and WAN.
To prevent cyber-attacks, enterprises need to inspect incoming and outgoing traffic for threats. Unfortunately, attackers are increasingly utilizing encryption to evade detection. With more and more applications using encrypted data, organizations that do not inspect encrypted communications are providing an open door for attackers to infiltrate defenses and for malicious insiders to steal sensitive data.
Per Cisco, it takes companies 100-200 days to discover an attack because 80 percent of security offerings cannot prevent threats within SSL traffic, while the average cost of a security breach has grown to $3.62 million globally. With an increasing level of data protection regulation, it is becoming vital for enterprises to be able to detect and mitigate an attack as quickly as possible.
SSL Decryption Challenges
Many network security and monitoring applications do not have visibility to encrypted traffic and cannot inspect the content of encrypted traffic. This creates dangerous gaps in corporate defenses or results in partial management and visibility of the network.
The few security and monitoring application that has embedded TLS decryption technology are not able to keep pace with the high demands of a high throughput environment. Moreover, TLS decryption is demanding in computational resources, that will divert resources from the application’s intended primary purpose. This may reduce the security tool throughput to a fraction of its performance without TLS decryption.
Additionally, security deployments typically use multiple appliances and applications to cover different aspects of cybersecurity. Often they process, inline or out-of-band, the same traffic flows. Having each tool perform its own TLS decryption independently, introduces significant performance and efficiency degradations throughout the deployment.
Niagara Networks’ Packetron for Optimum SSL Visibility
To meet decryption performance challenges associated with SSL proxy-based appliances, the network and security visibility layer needs to offload SSL decryption. Niagara's Network Intelligence layer can
efficiently offload SSL decryption processing tasks from SSL proxy appliances to the visibility layer through the introduction of new specialized capabilities in decryption and threat detection typically considered as beyond the scope of visibility layer capabilities
Niagara Networks’ Packetron – a packet acceleration module -- delivers high-performance SSL decryption as an integrated capability of Niagara’s intelligent network visibility layer. The Packetron is based on Intel x86 architecture and can be optionally deployed as a component of N2 modular packet broker platforms.
Niagara Networks are industry specialists in network visibility, providing advanced network solutions for the specific needs of individual enterprises and networks.
This technology allows for efficient decryption implementations that can both provide out-of-band and inline decryption / re-encryption capabilities so that you can reduce your exposure to encrypted security concerns. See Figure 2 for a representation of the flow of decrypted traffic sent for analysis.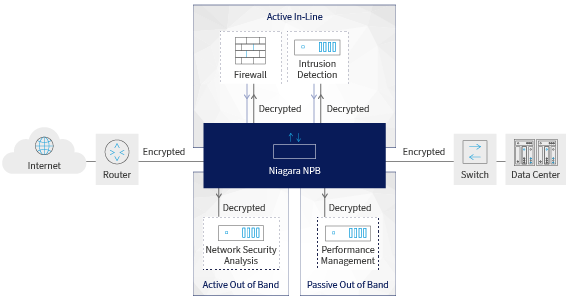
Figure 2. Niagara Networks Out-of-Band and In-Line TLS De-Cryption and Re-Encryption Capabilities
Niagara Networks are industry specialists in network visibility, providing advanced network solutions for the specific needs of individual enterprises and networks. Don’t leave your network vulnerable to security threats, schedule a consultation with one of our network visibility experts today to evaluate your SSL network visibility challenges.
-2.png)
 By: André Vink
By: André Vink