It’s time to implement bypass switches (or upgrade your existing ones) to ensure your inline network security devices are pulling their weight and offering your enterprise optimum stability and service.
Network bypass switches are designed to empower inline security and the high availability (HA) of the enterprise security suite of tools and devices. Amongst other things – which we’ll cover in this blog post – they are involved in scenarios of pervasive visibility and security tool efficiency. However, in order to find the best bypass matches for your needs, we must first understand what a bypass is, and what it can do for you, both in ensuring the resilience of your network security, and the enterprise’s business interests and return on investment (ROI).
What is a bypass switch?
A bypass switch is a special type of active device, that connects an inline device with a monitored network segment. The bypass switch (also known as a “bypass tap”, or just “bypass”) has two inter-related and critical business-functions: 1. It serves to check the health of active, inline devices (a security tool, for example). 2. If the inline tool fails (or it looks like there will be an imminent failure), then the bypass can reroute the traffic coming from the network device, so everything will continue to flow without interruption.
The bypass device contains a relay switch that eliminates the points of failure. Thus, if an inline network security device is not able to pass or process traffic (for example during a tool failure) it automatically bypasses it, by rerouting traffic around the device.
A power outage in a security device it is linked to, for example, will cause the relay to automatically close, and the switch then reverts to a 'bypass mode'. This mode guarantees business continuity and will prevent an inline tool from crashing the network (all or even part of it), and the rerouted data packets will then bypass the no longer responding inline device. Your network connection is thus assured continuity (high availability), and the issue can be dealt with ‘off-line’ without interrupting the network activity (this could entail carrying out maintenance, replacing or upgrading, or even disconnecting the non-functioning device).
The network bypass switch generates a series of continuous bi-directional heartbeat (HB) packets via the device ports. These are used to monitor the health of the inline device and enables the bypass switch to know what the state of a device connected to the bypass is – that is, to decide if it indeed needs to be bypassed.
While the HBs are returned, the traffic will continue to flow through the inline device. If the heartbeat is not returned by the bypass switch, or if the inline device is disconnected, loses power, or otherwise fails, the bypass switch will reroute the traffic directly between its other network devices, and bypass the device that is no longer in service. Data packets are therefore not dropped, and the traffic is ensured of continuously flowing on the network link.
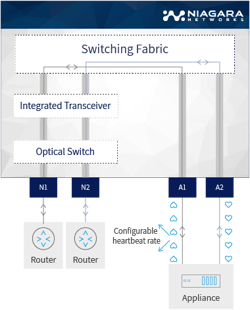
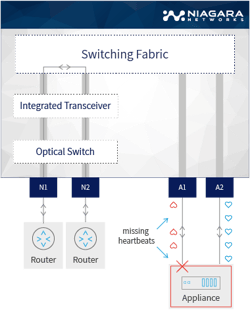
Once the heartbeats are again detected, then the bypassed security device can be brought back in-line (the bypass switches out of its ‘bypass’ mode and the relay returns to its pre-bypass position), and the traffic can again divert back to it.
Note that HB timeouts can also be set to ‘switch on’ the bypass device. In this way, not only full failure malfunctions but also just undesired slowdowns can be marked for a bypass. This may occur when there is a significant, unacceptable, slowdown (latency), for example, due to an overloaded network.
Some tools and devices have a degree of internal bypass functionality, however, this is usually not sufficient for high availability (HA) circumstances. This is because those devices’ internal – limited – operation usually do not have the bypass switches’ heartbeat functionality. This is essential for continuously measuring the ‘pulse’ to detect if the traffic of a device has gone down (when it fails), or if it is overloaded and slowing everything down, etc.
Bypass Switch Types - What you need to know
There are various types of bypass switches, each with its own advantages. The most common are:
- Optical bypass
- Bypass switch with individual switching fabrics (per segment)
- Bypass switch with common switching fabric
Each type of bypass switch has its advantages and disadvantages. To make the right match, you need to account for both the characteristics of the specific network node it is planned to be located at, as well as the overall network architecture and configuration.
Optical Bypass
The optical bypass is the most cost effective of the different types of bypass switches. It is an excellent fit for when you do not need a heartbeat or tap functionality, since it is a passive, optical device. Its main advantage is that it always functions, even if power goes out, since its strength lies in splitting light, and there is no actual power involved in its functioning.
Bypass switch with individual switching fabrics (per segment)
This type of bypass switch can be considered the classic bypass type. It works on the basis of heartbeat pulses that monitor the health of inline security devices. Based on a simple power on/off criteria (or a data streaming threshold), it can fail-over thanks to its power relay, to reroute the data traffic such that there is no packet loss whenever required (for example, during a power down of a monitoring device, due to failure, or maintenance requirement).
The monitoring and detection via heartbeat – as described previously – also empowers this type of network bypass switch to return the bypassed device back to service within the network.
Bypass switch with common switching fabric
The main advantage of a bypass switch with common switching fabric is the greater versatility across multiple bypass segments. For example, one of the things that the common fabric enables, is redundancy schemes schemes, where the bypass can reroute to a redundant device if one should go offline.
The bypass switch can be configured to do load sharing or handle traffic while maintenance is being carried out on a device dealing with the same segment. For example, you can configure one device or tool to be the primary, and one device or tool to be the secondary. With common fabric, the bypass switch performs a lot of the functions that a packet broker does.
What would a typical bypass scenario look like?
Bypass switches can be implemented in a range of scenarios. Here are a few examples:
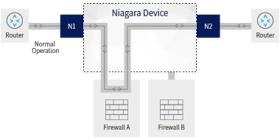
Scenario 1 - Normal bypass operation
The network bypass switch is placed between nodes N1 and N2, instead of the inline security device (here, the firewall) that is now connected to the bypass at nodes A1 and A2.
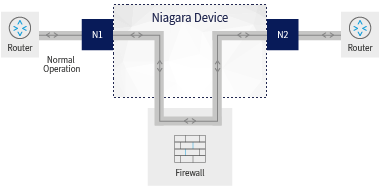
In normal operation, all the data traffic from N1 to N2 which would normally have passed directly through the security device, now first goes through the bypass switch.
The bypass switch feeds the security device via A1 and returns the security device’s data packets via A2 to N2. At the same time, the bypass switch is sending heartbeat pulses to the security device to check that it is OK.
So far, so good. Everything runs smoothly.
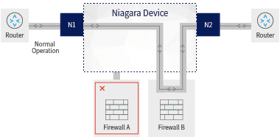
Scenario 2 - Bypass of Failed Inline Device
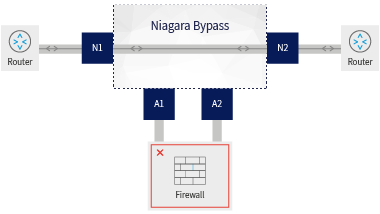
In this scenario (with the same setup as in the previous scenario), the security device (the firewall) that is connected to the bypass at nodes A1 and A2 has gone offline. This is where the bypass switch comes into play, and its relay automatically opens: the switch connects up nodes directly, making sure that the traffic between N1 and N2 remains up and running, so that there is no data loss between them.
Again: So far so good. Everything continues to run smoothly.
Scenario 3 - Bypass of Failed Bypass Switch
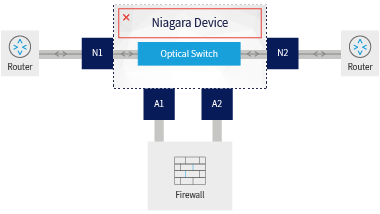
In this scenario, the bypass switch itself is not operational – due to a power outage. However,
the traffic between N1 and N2 continues to flow thanks to the bypass’ optical/copper relay.
Again: Everything continues to run smoothly.
Summary
Whether you are upgrading your existing network bypass switches, or adding new ones, you need them to enhance your overall network security suite and empower your inline security devices.
The different switch types offer diverse characteristics that can be selected for best-match with your inline security devices. Thanks to the bypass switch’s pro-active heartbeat mechanism that continuously tests if a device is ‘alive’ (and if it isn’t, it automatically and seamlessly bypasses it) – you are ensured robust high availability and stable and secure network activity for your enterprise.
In addition, since the switch always stays in the network, it can be placed into bypass mode as required, thus enabling security and monitoring devices to be added, removed, or upgraded as needed.
The bypass switches are easy to integrate into the network and offer essential health monitoring, offline/online control, and failover versatility for you to empower your inline security solutions. They represent a secure, simple, and affordable solution for your business continuity requirements.
.png)
 By: André Vink
By: André Vink